Exploiting Web Applications: Identifying Weaknesses and Vulnerabilities - Part 1
- prabhu p
- May 19
- 5 min read

Web Application: This acts as the interface between users and web servers through web pages. It enables users to request, submit, and retrieve data to/from a database over the Internet.
Basically it is,
I wandered through the skies, searching for you, The ocean called, and there you fell, When I sank, the sky rose for me.We need some things to know before Hacking:
1.Working of Web applications
Users access these services by entering the web application’s address (URI or URL) in a browser.
The browser sends the request to a server.
The server stores the web application data and displays it in the browser.
Popular web servers: Microsoft IIS, Apache HTTP Server, H2O, LiteSpeed, Cherokee.
Two side scripts — server side scripts , Client-side scripts.

1.1 Web Application Architecture.
Client/Presentation Layer
Includes devices like laptops, smartphones, and computers with operating systems and browsers.
Users enter a URL in the browser, sending a request to the web server, which responds and displays the web page.
Web-Server Logic Layer
Contains components like a firewall, HTTP request parser, proxy caching server, authentication handler, resource handler, and server hardware.
Manages security, handles client requests, and processes multiple requests simultaneously (e.g., IIS Web Server, Apache Web Server).
Business Logic Layer
Implements the functional logic of the web application using technologies like .NET, Java, and middleware.
Defines data flow, integrates legacy applications, and stores application data.
Database Layer
Includes cloud services, B2B layer for commercial transactions, and database servers.
Stores and supplies data as requested by the server using specific protocols.
(e.g., MS SQL Server, MySQL server)

1.2 Web services.
A web service is software deployed over the Internet.
Uses standard messaging protocols (e.g., SOAP) for communication between different platforms.
Integration:
Java-based services can interact with PHP applications.
Integrated with SOAP, UDDI, WSDL, and REST across the network.
Architecture:
Involves service provider, service requester, and service registry.
Operations include publish, find, and bind.
Roles:
Service Provider: Offers and publishes web services.
Service Requester: Seeks and invokes web services.
Service Registry: Stores and provides service descriptions.
Operations:
Publish: Service descriptions are published for discovery.
Find: Requesters obtain service descriptions.
Bind: Requesters establish communication with services using binding data.

I know this is a lot, No worries hacking is easy….
1.3 Vulnerability Stack
The 8 layers does this :
Vulnerability stack


This will be more fun , if you learn this — OWASP TOP 10 WEB APPLICATION ATTACKS — Introduction — OWASP Top 10:2021
Now lets doooooo hacking………..this is fun.
2.Hacking Strategies.
▪ Footprint web infrastructure ▪ Analyze web applications ▪ Bypass client-side controls ▪ Attack authentication mechanisms ▪ Attack authorization schemes ▪ Attack access controls ▪ Attack session management mechanisms ▪ Perform injection attacks ▪ Attack application logic flaws ▪ Attack shared environments ▪ Attack database connectivity ▪ Attack web application clients ▪ Attack web services.
2.1 Footpriting — Scanning WAP Reconnaissance using Nmap and Telnet
The below nmap command will bring the most of the Horroscope. lets attack my blog.
nmap -T4 -A -v www.binaryb.blog

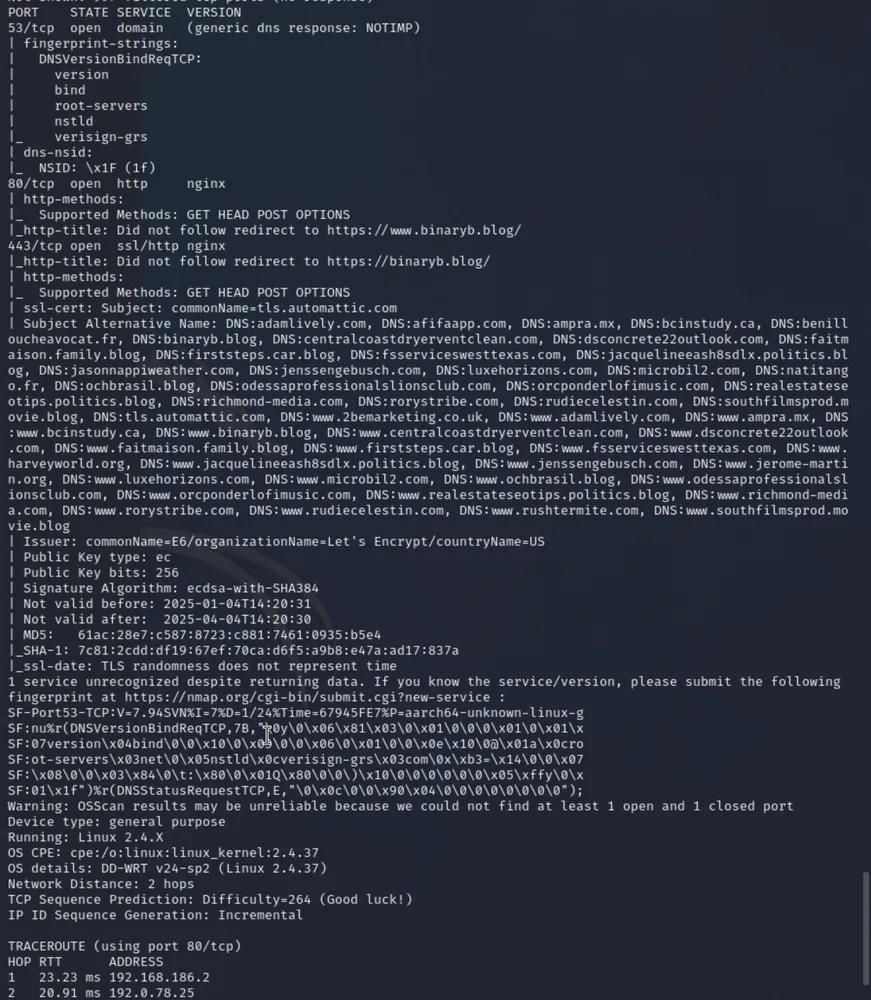
thats a lot of information!
What i found is :
Target Domain: www.binaryb.blog
IP Address: 192.0.78.25
Status: Host is up with a latency of 0.024 seconds.
DNS: Indicates another IP (192.0.78.24) but it wasn’t scanned.
Port 53/tcp: Open, running a DNS service (generic DNS response: NOTIMP).
Port 80/tcp: Open, HTTP service using Nginx (redirects to HTTPS).
Port 443/tcp: Open, SSL/HTTP service using Nginx with Let’s Encrypt SSL certificate.
Validity: 2025–01–04 to 2025–04–04.
Subject Alternate Names (SAN): Includes multiple domains (e.g., binaryb.blog)
Detected OS: Linux 2.4.X, possibly DD-WRT v24-sp2.
Reliability: OS detection is unreliable due to limited open/closed ports.
Network Distance: 2 hops.
Gateway: 192.168.186.2.
whatweb --log-verbose=binaryblog_report www.binaryb.blogThis runs WhatWeb in verbose mode and saves the detailed output to a file named binaryblog_report.
Purpose: Collect detailed information about the target website, including CMS, web technologies, frameworks, plugins, and possible vulnerabilities.

Report of the whatweb
What i found:
Initial URL: http://www.binaryb.blog
HTTP Status: 301 Moved Permanently
Redirects to: https://www.binaryb.blog/
Server: nginx
Uncommon Headers: x-ac, alt-svc
Notes: The website enforces HTTPS, and the server is identified as nginx. Uncommon headers like x-ac and alt-svc might indicate custom configurations or hosting provider settings.
HTTP Status: 301 Moved Permanently
Redirects to: https://binaryb.blog/
Server: nginx
Strict-Transport-Security (HSTS): Enabled (max-age=31536000)
Uncommon Headers: x-ac, alt-svc
Notes: The site has an HSTS policy enabled, which forces HTTPS connections. Another redirect occurs to https://binaryb.blog/.
HTTP Status: 307 Temporary Redirect
Redirects to: https://floramagnai.wixsite.com/binaryb
Server: nginx
Strict-Transport-Security (HSTS): Enabled (max-age=31536000)
Uncommon Headers: x-ac, alt-svc
Notes: The site redirects to a Wix-hosted page, indicating the use of Wix as the content management platform.
HTTP Status: 200 OK
Title: Home | BinaryBEE
IP Address: 34.144.206.118
Server: Pepyaka (Wix custom server)
Technologies Detected:HTML5MetaGenerator: Wix.com Website Builder
Scripts: application/json, text/javascript, wix/htmlEmbeds
Cookies: XSRF-TOKEN
Open-Graph Protocol: Enabled (for social media integration)
Email Addresses: Multiple found (e.g., 0e6a29e4756740a8a63493e912ba2174@sentry.wixpress.com)
Strict-Transport-Security (HSTS): Enabled (max-age=86400)
Via Proxy: Google
Notes: The website is fully hosted on Wix, utilizing their default configurations. Email addresses in the headers are likely tied to Wix’s internal error reporting or analytics systems.
2.2 Finding vulnerabilities — OWASP ZAP
OWASP ZAP (Zed Attack Proxy) is the superhero you didn’t know you needed! 🚀 Trusted by developers, testers, and security pros worldwide, this open-source marvel is like your personal bodyguard for web apps, sniffing out vulnerabilities before the bad guys do.

Alerts tab shows the vulnerabilities.
2.2.1 Finding Loadbalancers : Dig command
dig www.binaryb.blog
This shows the load balancers.
CNAME Record: The domain www.binaryb.blog points to binaryb.blog through a CNAME record.
Multiple A Records: Two A records (IP addresses 192.0.78.24 and 192.0.78.25) are associated with binaryb.blog, meaning traffic can be routed to either of these IPs.
Load Balancing or CDN: These multiple IPs indicate that the domain likely uses either a load balancer or a Content Delivery Network (CDN).
understand the port Uses in WAP in http services.
Whats next.


Identify Input Entry Points: Locate areas where user input is accepted, like HTTP requests or forms.
Identify Server-Side Technologies: Fingerprint technologies (e.g., ASP, PHP) running on the server to spot vulnerabilities.
Evaluate Server-Side Functionality: Analyze how the server executes scripts and processes requests.
Find Exposed Files/Directories: Use tools like Gobuster to uncover sensitive files and misconfigurations.
Spot Application Vulnerabilities: Identify flaws in the code that could be exploited.
Map Attack Surface: Identify and target vulnerable areas for exploitation.
2.3 Directories search for web pages
python3 dirsearch.py -u https://floramagnai.wixsite.com/binaryb -e aspx

Path Traversal Attempts: Multiple attempts to access paths like /etc/passwd suggest potential misconfigurations or unsanitized inputs.
Redirects & Invalid Files: Some URLs return redirects (302), indicating insecure URL handling or misconfigured routes.
Backup and Configuration Files: Files like .htaccess, .htpasswd, and aspx.old could expose sensitive information if accessible.
Potential Web Shell or Application Files: Files with extensions like .php, .cgi, .js, .json, .log, and .sql might indicate web shells or vulnerable scripts.
3 Map Attack Surface
vulnerability is the entry points, what we discovered in Owasp ZAP.
Once attackers identify entry points, server-side technologies, and functionalities, they can pinpoint vulnerabilities and map the attack surface of the target web application. This analysis aids attackers in planning their approach.


Perform Web Application Attacks
Let’s see in Part 2, where we’ll explore how to perform web application attacks on the discovered vulnerabilities.
This is where the real fun begins!

Comments