Art of Reconnaissance: From Battlefield to Browser — PART 0001
- prabhu p
- Dec 22, 2024
- 4 min read
Updated: Dec 24, 2024

Ancient and Medieval Techniques
Scouts and Spies: Greeks, Romans, and Chinese used scouts and spies to gather intel on enemies.
Assyrian Siege Techniques: Assyrians used advanced siege engines and psychological warfare to demoralize foes.
Roman Speculatores: Elite Roman soldiers conducted covert operations and gathered vital intelligence.
Renaissance to Early Modern Period
Cartography and Navigation: Renaissance advances in map-making improved reconnaissance for explorers and military commanders.
Galileo's Telescope: Galileo's telescope helped military commanders understand distant enemy positions.
18th and 19th Centuries
Napoleonic Wars: Napoleon's armies used cavalry scouts and spies for detailed enemy intelligence.
Balloon Reconnaissance: Civil War balloons provided aerial views of enemy positions, starting aerial reconnaissance.
20th Century and Beyond
Aerial Reconnaissance: WWI and WWII planes captured critical enemy intelligence from the skies.
Satellite Imaging: Cold War satellites allowed detailed surveillance of enemy territories from space.
Drones: Modern drones offer real-time aerial reconnaissance with high-resolution imagery.
Cyber Reconnaissance and Hacking:
Passive Reconnaissance: Gathering information from public sources without interacting with the target.Tools: OSINT platforms, WHOIS searches, DNS lookups, network sniffing.
Active Reconnaissance involves direct interaction with the target system to gather information. Tools include Nmap, port scanners, and vulnerability assessment tools.
Footprinting involves collecting detailed information about a target's network infrastructure. Tools include Recon-ng, Maltego, and social media monitoring tools.
Key Tools
Drones: For real-time aerial reconnaissance.
Satellites: For high-resolution imaging and surveillance.
Network Scanners: Tools like Nmap for scanning and mapping networks.
OSINT Platforms: For gathering publicly available information.
GIS Software: For integrating and analyzing geographic data.
AI Algorithms: For processing large datasets and predicting movements.
Encrypted Radios: For secure, real-time communication.
Portable Sensors: For on-the-ground data collection.

let's begin fun...
Iam planning to show the entire reconnaissance ways in this article, hence I split it into 5 parts. This is part 1 - Footprints through search engines.
0001: Perform Footprinting Through Search Engines
the first step is to gather maximum information about the target organization by performing footprinting using search engines; you can perform advanced image searches, reverse image searches, advanced video searches, etc. Through the effective use of search engines, you can extract critical information about a target organization such as technology platforms, employee details, login pages, intranet portals, contact details, etc., which will help you in performing social engineering and other types of advanced system attacks.
0001.0001 - Google Hacking Techniques.

Use the company name, organization name, and your name and find something.
For more Google Dorking links - visit my Github: prabhu31297/Google-Dorking
Exploit Database - Google Hacking Database (GHDB) - Google Dorks, OSINT, Recon
Takeaways :
Use Robots.txt: Prevent search engines from indexing sensitive data.
Limit Public Info: Avoid sharing personal details online.
Secure Your Website: Regularly update and use strong passwords.
Monitor Your Footprint: Search for your info online to see what's public.
Use HTTPS: Encrypt data on your website.
Remove Sensitive Content: Take down or restrict access to sensitive info.
Basic Idea: Don't use the exact name, phone number, or DOB in the email address, filename, website URL, and have one or multiple preferred names for you.
0001.0010 - Video and Image Metadata searching.
Analyze metadata from videos or images to uncover details like creation date, location, and device used.
Use metadata to enhance reconnaissance on a target for ethical or investigative purposes.
To get YouTube video metadata - MW Metadata.
MW Metadata tool enables fetching metadata like upload date, duration, tags, and descriptions. Ideal for gathering insights from YouTube videos quickly.

2. To fetch the metadata of the video file downloaded - MediaInfo
Tool: MediaInfo provides comprehensive technical details of video files.
Extracts codec, resolution, frame rate, and other embedded metadata.

3. Fetch some image metadata - From any social media images - ExifTool
Tool: ExifTool extracts metadata from photos, including GPS data, camera details, and editing history.
┌──(root㉿kali)-[~]
└─$ sudo apt install exiftool
0001.0011 - Gather Information from FTP Search Engines
Purpose: FTP search engines locate files on FTP servers.
Use Case: Industries, companies, and institutions utilize FTP servers to archive and share files.
Target Information: Business strategies, Tax documents, Employee personal records, Financial records, Licensed software, and Confidential directories.
Value: Provides insights into sensitive and critical organizational data.
My favorite FTP search engine - NAPALM FTP Indexer

0001.0100 - Gather Information from IOT Search Engines
Purpose: Crawl the Internet for publicly accessible IoT devices.
Information Provided: SCADA systems control, Traffic control systems, Internet-connected household appliances, Industrial devices, CCTV cameras
Significance: Exposes critical IoT devices and highlights potential vulnerabilities.
Types: Device Search Engines: Discover connected devices (e.g., Shodan, Censys, Thingful).
Information Search Engines: Focus on IoT topics (e.g., Topical IoT Search Engine).
Process: Data collection, indexing, and result display.

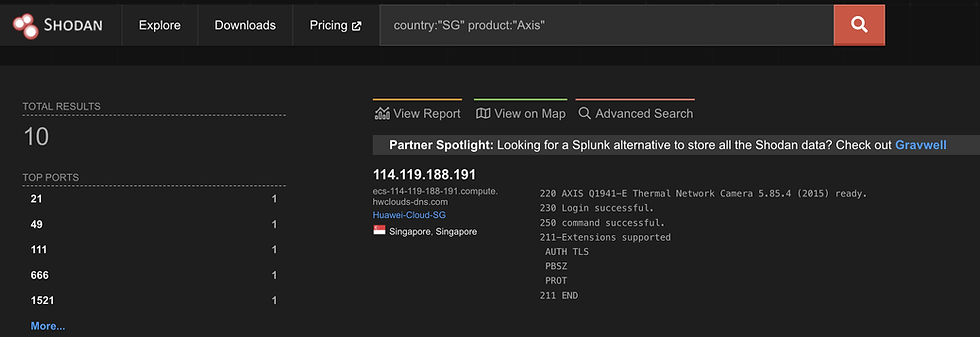
some commands:
webcamxp – Find exposed CCTV cameras.
smart thermostat – Locate internet-connected smart thermostats.
SCADA – Search for SCADA (industrial control) systems.
HVAC – Locate exposed HVAC systems.
Apache – Find web servers running Apache.
nginx – Search for Nginx web servers.
FTP – Find exposed FTP servers.
port:80 – Search for devices with port 80 (HTTP) open.
vuln:heartbleed – Search for devices vulnerable to the Heartbleed bug.
country:"US" – Filter devices located in the United States.
ssh – Find exposed SSH servers.
telnet – Search for exposed Telnet devices.
router – Locate exposed routers.
printer – Find exposed printers.
product:"Axis" – Search for Axis brand cameras.
Apache 2.4.18 – Locate servers running a specific Apache version.
cheatsheets - Shodan Cheat Sheet by sir_slammington - Cheatography.com
Ready for more? Let’s dive into Part 2!

Comments